The financial sector is undeniably a prime target for cybercriminals today. Holding a treasure trove of sensitive data like customer information and account details, financial institutions (FIs) are intrinsically vulnerable to such attacks. A 2024 report by the International Monetary Fund (IMF) suggests that cyberattacks in the financial sector pose a serious threat to global financial stability.
The report also notes that the financial sector is uniquely exposed to cyber risk, with the risk of extreme losses continuing to increase. A successful cyberattack cannot only disrupt daily financial services, but ultimately, cripple economic activities.
Read on to find out more about cybersecurity for financial institutions, strategies to combat the risks, and steps to create a risk management plan.
The Impact of Cyberthreats on Financial Institutions
Cybercriminals target various types of FIs, and the specific impacts can vary depending on the firm’s role in the financial system. To curate a risk management process that works, it’s critical to first understand how such threats can uniquely impact your institution.

Credit unions
Credit unions often have smaller IT budgets and less sophisticated security measures, and a successful attack can lead to a complete shutdown of online services. Last December 2023, about 60 credit unions in the US experienced outages due to a ransomware attack. This was just months after the National Credit Union Administration (NCUA) announced “a concerning rise in cyberattacks against credit unions, credit union service organizations (CUSOs), and other third-party vendors supplying financial services products.”
As credit unions typically rely heavily on member trust and community reputation, a data breach can result in a loss of trust. This is why it’s important to take immediate actions (e.g. investing in compliance software) to protect sensitive data and the financial well-being of the members.
Banks
On top of facilitating high volumes of transactions, banks also hold vast amounts of customer financial data. A cyberattack could lead to financial losses, may it be through fraudulent transactions and ransom payments. In 2023, four major European banks – Deutsche Bank, ING Bank, Postbank, and Comdirect – reported customer data leaks due to the MOVEit hack, one of the largest hacks in history.
Such supply chain attacks pose a serious threat to banks, particularly because their data typically relies on the risk practices of third-party entities. That said, banks should meticulously assess their partner’s security systems to prevent any liability in the event of a breach.
Insurance companies
Insurance companies manage sensitive personal data, including Social Security numbers, health information, and financial details. A cyberattack can expose such information, which puts customers at risk of identity theft and fraud. It can also disrupt critical insurance services and hinder claims processing.
In recent news, health insurance giant UnitedHealth Group confirmed a cyberattack on its subsidiary Change Healthcare and has paid over $3.3 billion to affected providers. Also, Fidelity Investments Life Insurance Company recently notified roughly 28,000 customers that their personal data had been compromised in a cybersecurity incident.
Brokerage firms
Like any other financial institution, brokerage firms hold valuable assets including customer data and investment portfolios. A breach in their systems could result in theft of customer funds, manipulation of investment accounts, and even unauthorized trading.
Just last March, Vietnam’s third-largest securities broker, VNDirect, reported a cyberattack on its system that suspended trading transactions. The broker service provider implemented a four-stage restoration process to decrypt the blocked data and restore floor trading and other financial services. Such attacks cannot only erode investor confidence in the markets but even disrupt actual financial markets.
Mortgage companies
A mortgage lending process involves handling sensitive corporate and customer data. Last March, Nations Direct Mortgage confirmed a data breach from late 2023, which leaked Social Security numbers and other data of 83,000 customers. Also, in late 2023, Texas-based mortgage giant Mr. Cooper dealt with a ransomware attack leaking the personal data of nearly 14.7 million people and forcing a shutdown on its systems.
Cyberattacks can have numerous consequences for mortgage firms, including disrupted credit checks, exposed borrower data, loan processing delays, and even regulatory fines.
Risk Management Strategies for Financial Services Cybersecurity
Cyber threats have acutely threatened the financial system over the years. This is why integrating an enterprise-wide approach to cyber resilience is crucial for financial institutions. In the World Economic Forum’s Global Cybersecurity Outlook 2024, 78% of respondents say that their cyber resilience approach is integrated into their enterprise risk management, significantly boosting the firm’s ability to handle security threats. Also, 90% of cyber leaders believe that cyber inequity requires urgent action.
Below are some strategies to incorporate into your financial services cybersecurity:
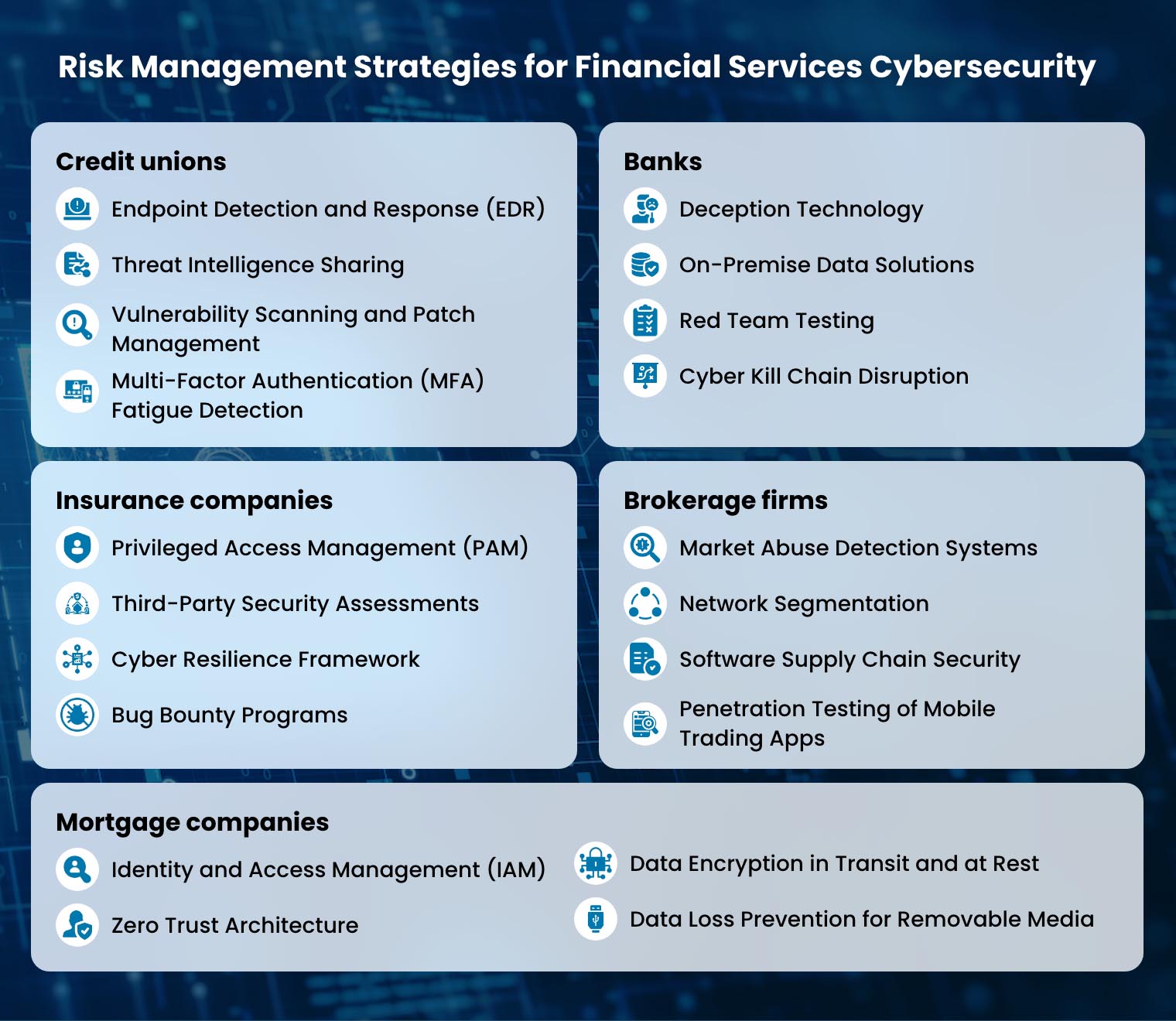
Credit unions
Focus: Limited IT budgets and less sophisticated security measures.
Risk management strategies:
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoints (e.g. laptops, desktops) for suspicious activity and automate incident response in case of an attack.
- Threat Intelligence Sharing: Consider partnering with other industry firms or Financial Information Sharing and Analysis Centers (ISACs) to share threat intelligence and stay updated on evolving cyberattacks targeting credit unions.
- Vulnerability Scanning and Patch Management: This involves scanning management software vulnerabilities and the deployment and verification of patches for credit union software systems. Such strategies are ideal for attack surface reduction and effective cyber hygiene.
- Multi-Factor Authentication (MFA) Fatigue Detection: Implement MFA solutions with mechanisms to detect and prevent MFA fatigue attacks (also known as MFA bombing) where attackers attempt to wear down users through repeated login attempts.
Banks
Focus: Large volumes of customer data and high-value financial transactions.
Risk management strategies:
- Deception Technology: Employ deception techniques to actively lure and analyze cyber attackers in a safe environment, allowing you to gather intelligence about their tactics. Deception technology works by tricking attackers after false resources and usually involves a notification system to record attacker activity.
- On-Premise Data Solutions: For centralized management and scalability, migrate security tools and data to on-premise solutions, such as Security Information and Event Management (SIEM), Cloud Workload Protection Platforms (CWPP), and endpoint protection platforms (EPP).
- Red Team Testing: This targeted penetration test mimics real-life threats to identify how far the attacker can penetrate the system. Engage red teams or simulated attackers to identify potential weaknesses in the bank’s security posture.
- Cyber Kill Chain Disruption: Cyber kill chain (CKC) is a cybersecurity model designed to understand the different phases of an attack; reconnaissance, weaponization, delivery, exploitation, installation, command and control, actions on objective, and monetization. Developing strategies to disrupt such phases can make it difficult for attackers to succeed.
Insurance companies
Focus: Sensitive personal information and data privacy.
Risk management strategies:
- Privileged Access Management (PAM): This strategy involves enforcing strict controls around privileged accounts and permissions for users and systems, ensuring employees only have the necessary access levels to do their tasks.
- Third-Party Security Assessments: Conduct security assessments of vendors and partners before integrating their solutions into the software systems.
- Cyber Resilience Framework: Adopt a cyber resilience framework like the NIST Cybersecurity Framework or NERC-CIP to guide risk management activities and improve overall preparedness.
- Bug Bounty Programs: Implement bug bounty programs to incentivize ethical hackers to identify and report vulnerabilities in the software systems. Such programs can be done on top of the regular penetration testing.
Brokerage firms
Focus: Online trading platforms and customer investment accounts.
Risk management strategies:
- Market Abuse Detection Systems: Use market abuse detection systems to check for fraudulent trading activities that might exploit vulnerabilities in trading platforms. Some market abuse behaviors include spoofing or making fake orders, front-running, insider dealing, and wash trading.
- Network Segmentation: Segment the network into subnets to isolate critical systems and accounts from publicly accessible areas. This improves access control for internal and external network security, and performance due to less congestion in network traffic.
- Software Supply Chain Security: Implement measures to secure the software supply chain by verifying the integrity of software updates and patches before deployment. These may involve continuous testing of deployed software systems or validating checksums (e.g. developer tools).
- Penetration Testing of Mobile Trading Apps: Conduct regular penetration testing of mobile trading applications to identify and address vulnerabilities that attackers could exploit.
Mortgage companies
Focus: Personal information of loan applicants, loan processing systems, and compliance software.
Risk management strategies:
- Identity and Access Management (IAM): IAM offers secure access to resources such as data and emails by accurately verifying a person’s identity and permissions for the access attempt.
- Zero Trust Architecture: Move beyond traditional perimeter defense and implement a zero-trust architecture that continuously verifies user and device identities before granting access.
- Data Encryption in Transit and at Rest: Encrypt all mortgage application data, both while it is being transmitted (in transit) and when it is stored (at rest) to minimize the impact of a data breach.
- Data Loss Prevention for Removable Media: Implement controls to prevent unauthorized data transfer through removable media (e.g., USB drives) used by employees. Some solutions to consider are the BitLocker Drive Encryption (Windows), Apple FileVault (Mac), and other third-party encryption tools.
Creating a Risk Management Plan: Step-by-Step Guide

Whether you’re preparing for a new project or the organization’s entire financial services cybersecurity, it’s important to have a risk management plan ready. Here are some steps to help you create an effective one.
1. Identify the risks
Risk identification is the first step in crafting a risk management plan. Consult your teams, stakeholders, and key vendors to effectively identify potential risks. This brainstorming gives you different points of view on what causes or drives a risk event. For one, consider the current industry risks within your sector and how other organizations are addressing them.
It would also be helpful to analyze past projects or review historical data to check on risks that have materialized before. Did you have project delays due to unauthorized actors gaining access to sensitive data? What measures were implemented to rebuild lost data or retrieve system access? List down the risks and use a scoring system or a risk matrix to categorize their severity.
2. Create a risk register
Once you have a list of the potential cyber risks, it’s time to carefully assess them. Create a risk register to store all the necessary information such as risk description, risk score (based on the likelihood and impact of risks), mitigation strategies, and risk owners. Some risk scenarios you can rank by priority are data security, theft of materials, scheduling delays, and communication issues.
A risk register is a written document that can also be beneficial to prioritizing risks with the most damaging impact. It is usually maintained by a project manager and must be reassessed regularly.
3. Assign risk owners
Next, it is imperative to assign a risk owner who will be accountable for monitoring each identified risk and reporting on the risk status. The risk owner should also have the authority to take necessary actions to mitigate risks, such as resource allocation or decision-making. Any mitigation plan created by risk owners, however, should still be approved by stakeholders prior to implementation.
4. Develop the risk response plan
For each risk, it is ideal to have a specific response plan outlining the actions you need to take. Your response plan should take these approaches into account:
- Avoid: Configure mitigation strategies to eliminate the risk.
- Transfer: Shift the risk ownership within the team or company, or to an external party.
- Reduce: Lessen the likelihood or impact of the risk with the right actions.
- Accept: Make adjustments to handle risks that are unavoidable or with minimal impact.
Moreover, define the triggers that indicate the risk is materializing, allowing risk owners to know when to initiate the response plan. For instance, a failed login attempt exceeding a certain number of retries might trigger a suspicion of a brute-force attack.
5. Monitor risks continuously
Bear in mind that risk management is an ongoing process. Therefore, regularly reviewing your risk register, monitoring risks, and updating the response plan is necessary. For continuous monitoring, schedule periodic risk reviews (e.g. monthly or quarterly) to assess the effectiveness of mitigation strategies and identify any new risks. Additionally, don’t forget to update the risk register as you gather new information along the way.
Convene: Secure Board Meetings and Data Management
Safeguarding sensitive data is paramount, especially as cyberattacks post a constant threat. Financial institutions should find ways to prevent their consequences, and one is taking advantage of technology — such as board management software. Besides enhancing overall cybersecurity measures, board technology can also improve governance and regulatory compliance with ease.
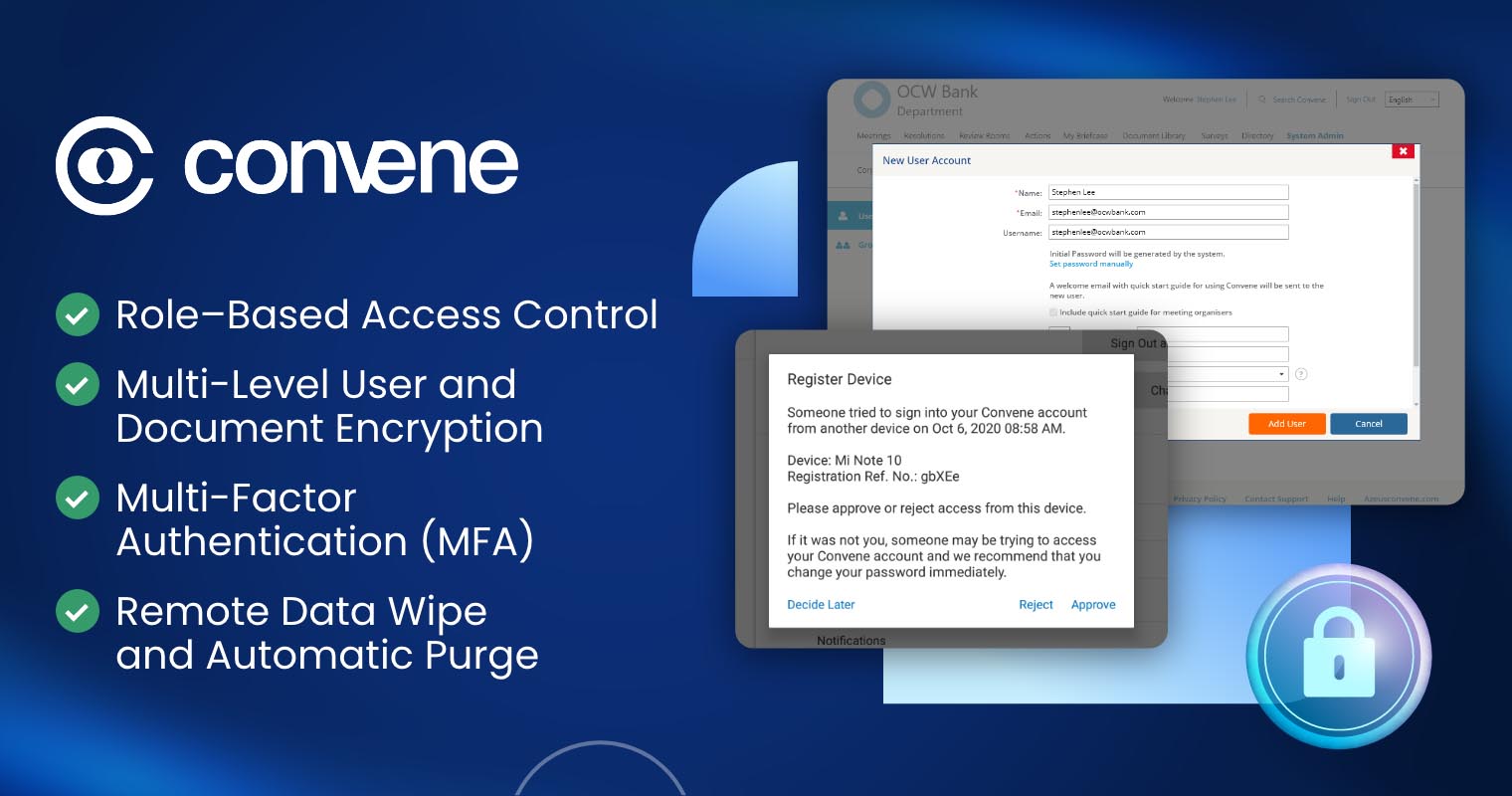
Convene, a leading board management software, is designed to conduct meetings and centralize board materials on a secure platform — supporting stronger cybersecurity for financial institutions. Some of Convene’s robust secure features include:
- Role-Based Access Control: Ensures only authorized users have access to files or data based on their predefined roles and permissions.
- Multi-Level User and Document Encryption: An industry-standard encryption to safeguard documents and data, at rest and in transit.
- Multi-Factor Authentication (MFA): An extra layer of security that requires users to provide a secondary verification, preventing the risk of unauthorized access attempts.
- Remote Data Wipe and Automatic Purge: Allows administrators to remotely wipe data from lost or stolen devices and enable automatic purging to eliminate outdated documents after a specified timeframe, minimizing data exposure.
Want to know more about Convene and its features? Reach out to our team and book a demo now!
Jielynne is a Content Marketing Writer at Convene. With over six years of professional writing experience, she has worked with several SEO and digital marketing agencies, both local and international. She strives in crafting clear marketing copies and creative content for various platforms of Convene, such as the website and social media. Jielynne displays a decided lack of knowledge about football and calculus, but proudly aces in literary arts and corporate governance.











