Cyber crime in the digital world has become a pervasive threat and the stakes for Australian organisations couldn’t be higher. The latest statistics from the Australian Signals Directorate (ASD) paint a vivid picture: a 23% surge in cyber crime reports compared to the previous year, with a staggering 94,000 incidents recorded in the financial year 2022-23 alone. What’s more alarming is the 14% increase in the average cost of cybercrime per report – $71,600 for large businesses, $97,200 for mid-size businesses, and $46,000 for small businesses.
These figures underscore the urgent need for directors and governance officers not just to understand the threat of cyber attacks but to act upon strengthening their cyber defences. Cyber security is no longer a luxury but a board’s priority.
In support of this imperative, the Australian Institute of Company Directors (AICD) and Cyber Security Cooperative Research Centre (CSCRC) partnered to develop Cybersecurity Governance Principles. These principles serve as a beacon of guidance, equipping directors and executives with skills and tools for cyber security governance.
Operationalizing AICD’s Cyber Governance Principles: Practical Steps
AICD’s Cyber Security Governance Principles’ goal is to offer a practical framework on how boards and businesses can adeptly navigate the complexities of cyber security in Australia from a top-down approach. Below are the five principles of cyber security to help you develop best practices.
Principle 1: Set clear roles and responsibilities
Change and action always start at the head of your organisation. Thus, the first principle focuses on establishing clear roles and responsibilities for both your board and management in contributing to overall cyber resilience.
Within this framework, both the board and management share oversight and accountability for how security risks are handled and governed. The board exercises effective oversight by delegating cyber risk management to the management or relevant subcommittees, while equipping themselves with the necessary skills and understanding of cyber security. The management, on the other hand, should be hands-on in driving cyber strategy and overseeing implementations and unit responsibilities. Annually evaluating and updating both roles is essential in ensuring the organisation keeps up with the evolving cyber landscape.
Additionally, accurate board reporting on cybersecurity can strengthen complete board oversight. Through this, directors can acquire insights into controls, data, and processes on cyber resilience. Regular presentation and discussion of these reports by management facilitate informed decision-making, particularly concerning internal and external cyber risks, emerging security trends, and overarching strategies.
By setting clear roles and responsibilities, organisations construct a solid framework for effective cyber security governance. This ensures that all stakeholders understand their roles in managing cyber risks and fortifying the organisation’s overall cyber resilience.
Principle 2: Develop, implement, and evolve a comprehensive cyber strategy
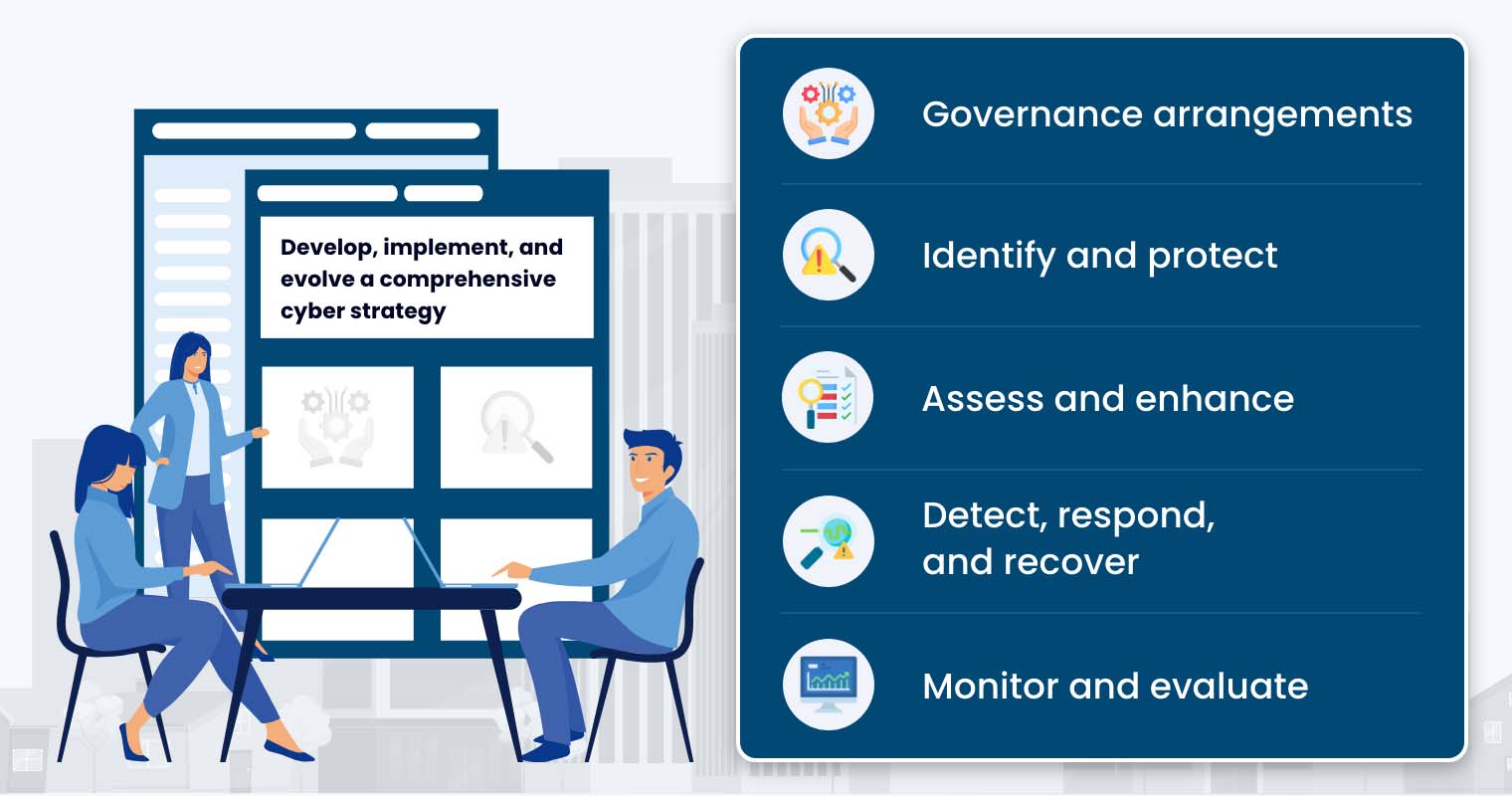
Once roles and responsibilities have been established, it’s time to act upon your current cyber situation. It is important to assess your internal capability by formulating a cyber strategy. This ensures that key digital assets and infrastructure are secure, and core IT personnel and processes are in place. Ultimately, this strategy must articulate how the organisation will respond to a cyber incident, facilitating operations and communications with stakeholders.
AICD outlines the key components of an effective cyber strategy, which include:
- Governance arrangements — Effective cybersecurity governance tailored to the organization’s size and complexity is paramount. This encompasses robust data governance practices, focusing secure storage of customer and organizational data while adhering to relevant legislation.
- Identify and protect — Key digital assets, such as critical customer and employee data and operational infrastructure, demand heightened protection. The cyber strategy should identify these digital assets and detail the processes to secure them.
- Assess and enhance — An accurate assessment of the organisation’s internal cyber capability, including core personnel, existing IT infrastructure, controls, and business continuity planning, can provide insights into where enhancement is needed. Cyber enhancements may vary from reinforcing cyber training, utilising external experts, to investing in new IT systems.
- Detect, respond, and recover — A substantial chunk of your cyber strategy should be dedicated to the plans and processes to detect cyber incidents, respond to attacks, and facilitate organisational recover.
- Monitor and evaluate — Regular review of the performance against the strategy can help determine where else to improve. While formal evaluations may occur annually, ongoing monitoring should be conducted periodically to ensure alignment with the organisational needs.
For some SMEs and NFPs, comprehensive cyber strategies may not be necessary as opposed to larger enterprises. However, industries like healthcare may require a documented cyber strategy to ensure they regulatory compliance and maintain cyber resilience.
Principle 3: Embed cyber security in existing risk management practices
The third principle emphasises the integration of cyber security into existing risk management practices within organisations. This involves identifying your organisation’s cyber-risk appetite – the level of security risk you’re willing to take in your digital operations to achieve business goals. A balanced cyber-risk appetite recognises the inherent vulnerabilities pervasive in this digital economy while weighing the potential benefits against the associated risks.
Central to an embedded approach to risk management is developing and overseeing risk controls – mechanisms designed to avoid (avoiding risks by eliminating specific activities), mitigate (mitigating risks by implementing internal or external controls), and transfer (transferring specific elements of risks to external parties) cyber threats. Security standards in Australia including the Australian Cyber Security Centre’s (ACSC) Strategies to Mitigate Cyber Security Incidents provide a guide on cyber risk controls for large and small organisations. Additionally, common risk management practices like external audits, penetration testing, and traditional risk-control frameworks (e.g. three lines of defence model) can be readily implemented to manage cyber risks.
Echoing Principle 2, the management must engage in periodic reporting and monitoring of the performance of risk controls. Assess attempted cyber incidents and incidents from other organisations to evaluate whether risk controls need to be optimized. Moreover, both the board and management should regularly reflect on whether the cyber-risk appetite remains applicable given the evolving internal weaknesses and external threats.
Principle 4: Promote a culture of cyber resilience
Fostering a culture of cyber resilience requires a collective commitment starting from the board and management. The fourth principle stresses that oversight of cyber security in Australian organisations must cascade into day-to-day operations. Cybersecurity isn’t solely a technical matter but also a cultural one, necessitating active involvement and participation from all levels.
Cyber security policies alone are not enough to promote cyber resilience; ongoing training and education are also as crucial. Annual training sessions for boards and staff should be a mainstay, ensuring organisational security practices are up-to-date. Additionally, directors must cultivate cyber literacy to stay abreast of the changing regulations on cyber security in Australia. Key regulatory bodies to review are the OAIC, APRA, and ACSC.
By championing awareness, shared responsibility, leadership, and ongoing improvement, organisations can establish a solid groundwork for cybersecurity resilience. This holistic approach ensures cyber security is ingrained in the DNA of the organisation.
Principle 5: Plan for a significant cyber security incident
The final principle acknowledges that despite preventive measures, organisations may still experience major incidents capable of disrupting operations and posing significant risks to the business. That’s why preparation is paramount to respond and recover effectively. A well-crafted cyber incident response plan serves as the cornerstone, highlighting the roles and responsibilities of the board and the staff during times of crisis.
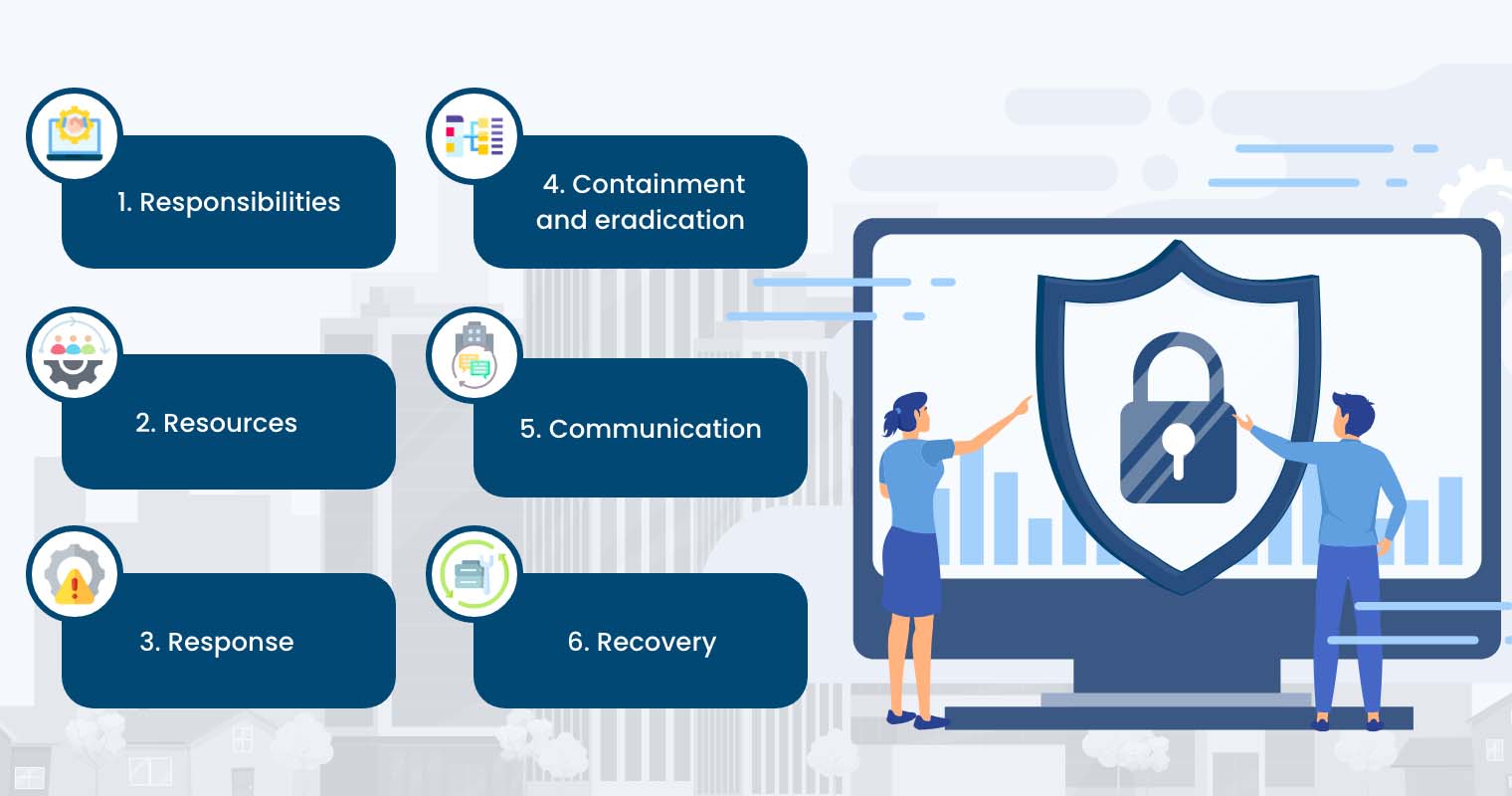
What should be included in your response plan are the following:
- Responsibilities — Establish who should be involved in implementing the response plan, comprising representatives from IT, communications, legal, executive management, and potentially third-party experts. Specify their responsibilities and authorities.
- Resources — Define the resources needed by the personnel, covering physical resources, key internal expertise, and external support from experts and partners.
- Response — Detail the steps in identifying and assessing a cyber incident’s impact on business operations and stakeholders (customers, employees, partners, vendors, suppliers, etc.). Emphasize the importance of immediate notification to external cyber incident response experts and government agencies.
- Containment and eradication — Outline the strategies for limiting the scale of potential cyber incidents. Delineate the steps to contain and eradicate the cyberattack.
- Communication — Establish dedicated communication channels for internal staff, law enforcement agencies, media, affected customers, and other stakeholders including the public. It is important to be transparent and accountable, particularly regarding the organization’s handling of the incident.
- Recovery — Specify the steps for rebuilding the data infrastructure and recovering losses. Include also here steps in identifying the lessons learned from the incident to inform future risk mitigation strategies.
By crafting robust incident response plans and conducting training and testing exercises, organisations can effectively mitigate the impact of cyberattacks and safeguard their operations and assets.
Empowering Cyber Security for Australian Organisations
The AICD’s Cyber Security Governance Principles provide a blueprint for directors and executives to navigate the complex cyber landscape and mitigate risks effectively. Boards and management have the responsibility to exercise oversight of cyber security and implement robust plans to mitigate risks.
To support the boards in upholding cyber security governance, leveraging a board portal can be instrumental in ensuring efficient collaboration, transparency, accountability, and security. Convene, the trusted board portal by Australian organisations, takes pride in providing meeting and management tools to help you champion the principles of cyber security by AICD. Built by a CMMI Level 5 company and powered by the Amazon Web Services (AWS), out board management software guarantees the highest level of safety, security, and data integrity. What’s more, Convene is accredited by the Australian Government’s Information Security Registered Assessors Program (IRAP), ensuring you utilise secure and compliant digital solutions.
Gain the peace of mind you deserve with your data and systems with Convene. Book a demo with us today!
Audrey is a Content Marketing Specialist at Convene, in charge of managing the production of quality content on the company’s website. A communication major keen on marketing, Audrey has been constantly seeking approaches to create tailored content—may it be about governance, digitalization, boards, or meetings—fit for the stakeholders. When not strategizing on the next ebook to produce, Audrey finds solitude in reading make-you-ugly-cry novels and listening to self-improvement podcasts.









